Data centers appliances, office devices and other wired computer systems are connected to switches and routers. A LAN Turtle is a microcomputer disguised as a USB ethernet adapter which is placed in between the UTP network of such a connected system. Next, the USB LAN Turtle ethernet adapter acts as a covert backdoor and can intercept traffic as a MiTM (Man-in-The-Middle). A LAN Turtle can also spawn a connection out to a malicious C2 server once it is placed in a routable network.
This blog post described how a Hak5 LAN Turtle can act as a covert backdoor to call multiple reverse shells. This way you have more than one try of getting a call-back in case one shell gets either detected, blocked or terminated. As a requirement, the malicious actor or insider threat must first manually install/plugin the LAN Turtle device to a USB port. Picture 1 shows how such a MiTM scenario is realized on an office printer.

Figure 1: Hidden MiTM device on a printer
Reverse Shell
A reverse shell is a remote interactive shell for command execution initiated by the attacker to gain control over a compromised system. A reverse shell can also be abused by an insider threat to exfiltrate data over a covert channel. Corporate edge and core firewalls are typically configured to filter/deny/block TCP and UDP ports, or even specific applications by applying layer 7 firewalling. Figure 1 shows how a well-configured firewall should block a traditional TCP or UDP reverse shell over port 4444:
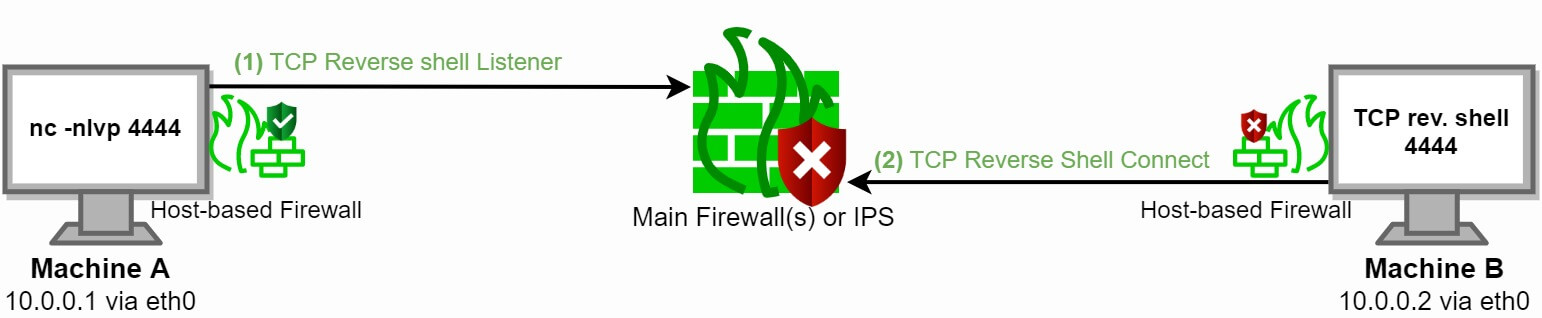
Figure 2: Firewall blocks a reverse shell over port 4444
As seen in figure 2, a reverse shell by itself can easily fail or get detected. A mechanism of spawning multiple automated shells is an ideal solution if you cannot determine which ports are open and can be used for spawning a shell.
Spreading the odds
Since the LAN Turtle runs on a Linux kernel, a custom script can be initiated to spawn multiple reverse shells in a logical order. crontab and netstat are your friends here. In case one reverse shell fails, a new reverse shell is automatically spawned to the C2 server with a small delay. Once a reverse shell is spawned successfully, a malicious entity or pentester has access to the network in which the locally connected host resides. This is shown in figure 2. Once connected, lateral movement can be initiated to further compromise the network and other systems.
In more depth, the first reverse shell can try to evade the firewall and IPS/IDS systems by leveraging DNS over UDP port 53. The second reverse shell can spawn an encrypted TLS session over port 443. Lastly, an ICMP reverse shell can be initiated. Figure 3 visualizes this mechanism. Keep in mind that you can also abuse legitimate cloud services for spawning a reverse shell.
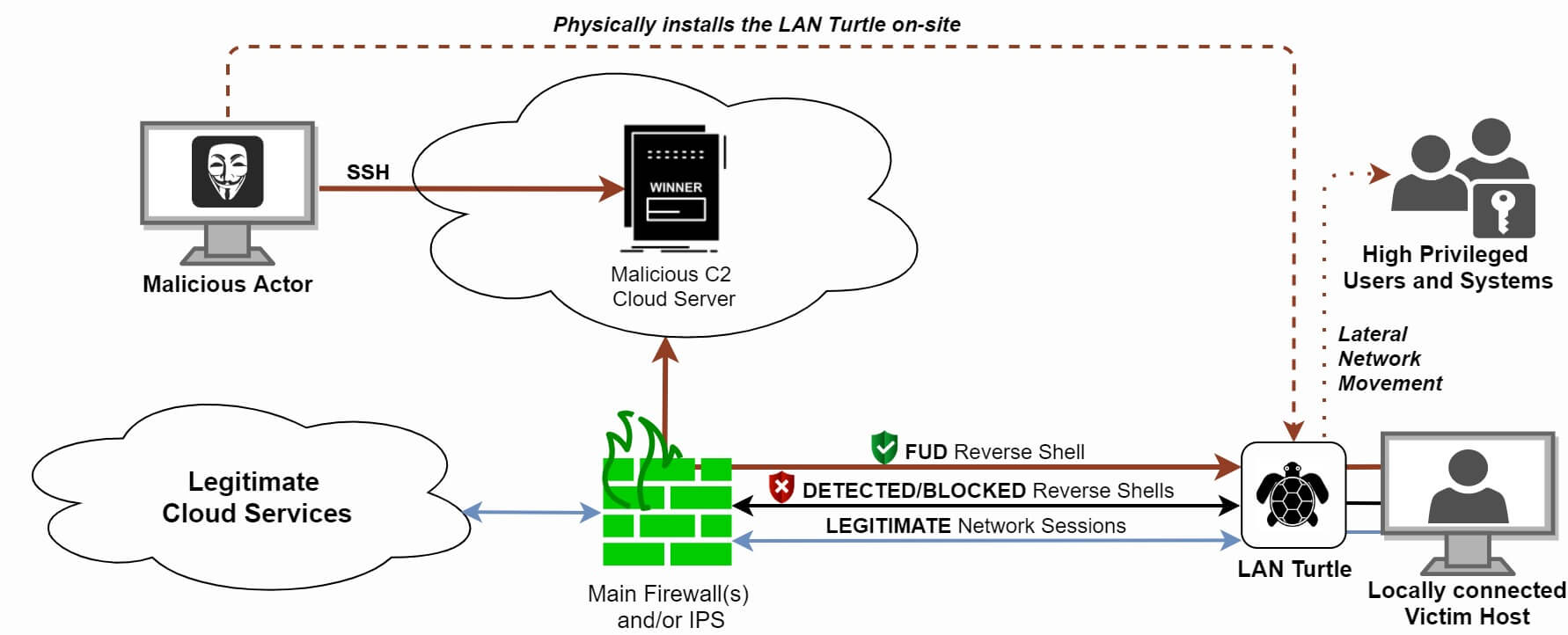
Figure 3: Multiple reverse shells spawned on a LAN Turtle
Detection
The LAN Turtle is a powerful offensive tool which can be rather effective in certain engagements. Depending on the quality of your reverse shell, a LAN turtle can be either hard or easy to detect by your SOC/IPS/IDS. You can also leverage a HIDS to detect new or unknown network interfaces (NICs) being added to your systems. However, the LAN Turtle leverages a Realtek chipset. This makes it harder to distinguish a legitimate (v)NIC from a rogue one.
Make sure to physically check for these kinds of rogue devices in your infrastructure on a periodic basis. Also create thorough network segmentation to prevent lateral movement. A honeypot could reveal lateral movement and someone poking around in your network.





