The vast majority of large organizations and enterprises have a predominant Windows 8/10 client estate for their employees. With more and more security threats on the horizon, the right IT security framework can prevent a significant portion of security incidents such as ransomware attacks and implants to steal confidential information.
On your Windows client domain, security controls should be deployed and enforced to detect and block malicious threats. However, security controls are commonly operated by departmentalized security analysts, which results in a slower reaction time for further mitigation steps. Organizations sometimes do not correlate security alerts from these different security solutions at all.
This blog post elaborates on an in-depth security framework based on five pillars that detect, block and prevent security threats on Windows clients.
Why implement a security framework
Let's first take a few steps back. What is a security framework and why does your organization need one? A security framework defines best practices on security controls which should help to define your overall enterprise security program. Once you acknowledge your organization has security risks, you can map security threats against the security controls. This risk-based approach should materialize into a security roadmap according to your core business and outside pressures. You can either build your security program from scratch or implement other frameworks such as ISO 27001, COBIT, NIST CSF and 800-53, CIS, or even pull security controls from multiple frameworks.
Workstation security control framework
Mitigating security risks is an on-going iterative cycle. It is therefore important to adjust your security framework to real-world threats. This section describes our Windows workstation security framework, which can either land on top of industry-standard frameworks, or is adopted with any other security framework to shapes your security program.
We define a collaborative set of five core security controls that act as building blocks for our Windows workstation defensive security framework. This way you do not rely on a single security control for a certain threat also referred to as security in-depth. Our framework detects, blocks and prevents threats on Windows workstations. You can also make this framework part of your security growth plan if you cannot implement this framework straight away.
Figure 1 shows this technical security framework to defend your Windows workstation estate against common security threats based on MITRE ATT&CK (Adversarial Tactics, Techniques, and Common Knowledge) real-world observations. The MITRE ATT&CK model helps us lay out the possible steps an attacker has to take to achieve their goal(s). You should map out this matrix against your Windows environment. This should results in a reduction of the overall security risk exposures by preventing and detecting the ATT&CK Kill Chain Tactics, Techniques and Procedures (TTPs).
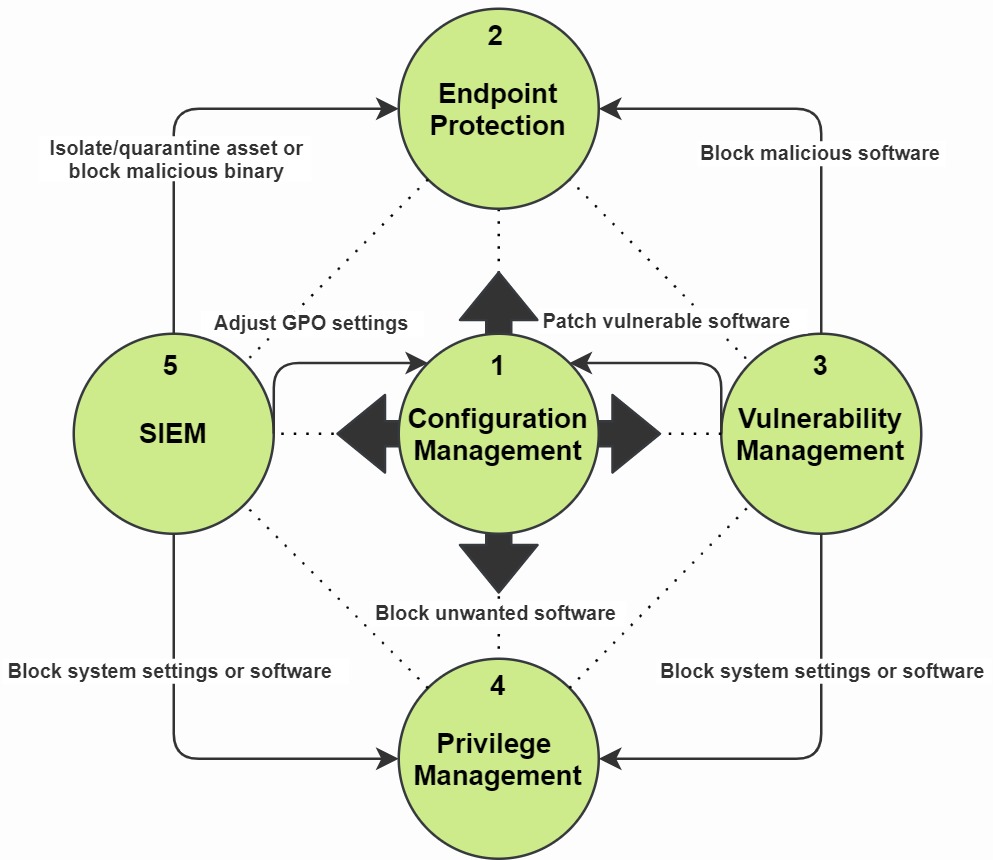
Figure 1: Windows client defensive security framework to detect, block and prevent threats
Let's go over each security pillar of this framework in more detail with some real-world examples:
1) In the center of our framework lies the Configuration Manager (CM) platform. This CM platform should force domain users to authenticate into a controlled desired state Windows environment where GPOs (Group Policy Objects) are deployed. GPOs can be used for hardening, such as block macros and enforce a supported default web browser. Furthermore, CM should provide whitelisted software provisioning, software updates and a Windows patch management process. Your CM should also be able to report back with its compliance status for all outstanding patches and its associated client assets such as a laptop or a VDI.
2) The EPP (Endpoint Protection Platform), also known as the ATP (Advanced Threat Protection) security control, should detect and block malware and quarantine suspicious binaries. Approximately 94 percent of malware was delivered via e-mail. This makes a resilient EPP solution of vital importance. Endpoint protection should also be leveraged to investigate threats that have already landed within your client estate. Third-party threat indicators, such as threat reports, can also be mapped based on alerts of certain known signatures or system behavior. Data from your SIEM (5) can be used to correlate and perform further security or forensic investigations. You can also decide to block system actions or software based on known exploitation paths (4).
3) Approximately 60 percent of security breaches involved vulnerabilities for which a patch was available but not applied. A vulnerability management agent performs periodic scans on your assets. A vulnerability agent will scan installed software, Windows system settings (changes) and open ports which can make your client estate more vulnerable. A vulnerability scanner also measures your current Windows patch level. Next, your vulnerability tooling can categorize known vulnerability within your client estate based on Common Vulnerability Scoring System (CVSS) criticality and asset count. From time to time, your patch management process (1) did not cover all your assets or even failed. This means not all assets are provided with security patches which means Windows can get stuck at a certain patch level. This means remediation should be set out by the configuration management platform. This way we minimize our attack surface.
Another example - let's say an employee installed a cracked version of Adobe Photoshop on his asset which does not update anymore and even came with a *little surprise*. This means your Endpoint Protection (2) solution has to block and remove this Trojan. Lastly, deprecated software which no longer has security patches available (e.g. Microsoft Office 2010 and old versions of Adobe Reader) should be removed and block in with our next security control (4). Deprecated software can be prone to Remote Code Execution (RCE) or a privilege escalation vulnerability, which can undermine the next security control.
4) An Endpoint Privilege Management agent plays a key role in maintaining the least privilege principle by removing (local) admin rights. The Endpoint Privilege agent enforces application control by creating whitelisted, blacklisted and gray-listed software combined with software versions. This way you can reduce your threat landscape by limiting the flavors of allowed software and block software from unknown sources. Let's take the following example. A DLL or executable might be flagged in your EPP as a Potentially Unwanted Program (PUP). You can either break the application, together with its potential uninstall process by quarantining the flagged file(s), or force an application block and initiate an uninstall with your Endpoint Privilege Management platform. Lastly, the Endpoint Privilege agent should also prevent employees from disabling Windows security controls such as Windows Firewall, (User Account Control) and uninstall any of the listed security agents.
5) Event logging should be forwarded to a centralized SIEM (Security Information and Event Management) monitoring system. This way suspicious behavior on client assets can be monitored. The SIEM can also fetch data from an IDS (Intrusion Detection System). The goal here is to gain more visibility of the attacker's behavior. Based on SIEM use-cases, alerts can be created and further action can be taken. This process is also known as threat hunting based on the "pyramid of pain" principle. Next, a blue team security analyst might use EPP (2) to block a binary or quarantine a client asset to prevent further lateral movement. Also, a blue team analyst can decide to further lower user privileges by changing policies in your endpoint privilege security control (4) or sharpen GPO policies (1).
Client security control solutions
Please note that the right processes, integration and mandates should be in place in order for this framework to succeed within your IT security operations. The actual security products of these five security controls are irrelevant as long as there is no vendor lock-in. Nonetheless, here are some non-sponsored/non-biased solutions for each security control:
1) Configuration Manager - Microsoft SCCM
2) Endpoint Protection Platform (EDR) - MDE (Microsoft Defender for Endpoint)
3) Vulnerability Management - Qualys Cloud Agent
4) Endpoint Privilege Management - CyberArk Endpoint Privilege Management
5) SIEM - By using Sysmon, Windows event logging should be forwarded to a centralized ELK or Sentinel SIEM.
You might be thinking that MDE as an EPP can also perform vulnerability scanning, and Windows SCCM can also block software with AppLocker. This however is not the point of this framework. Malicious actors can obfuscate a reverse shell or a RAT (Remote Access Tool) such that your MDE will not detect it, but could have been prevented by mitigating a vulnerability in-time or picked up by a SIEM use-case according to its MITRE ATT&CK attack path.
Credits for revising go to Remko van der Wal - IT security architect at Deloitte Europe.





